Efficient Homomorphic Integer Computer from CKKS
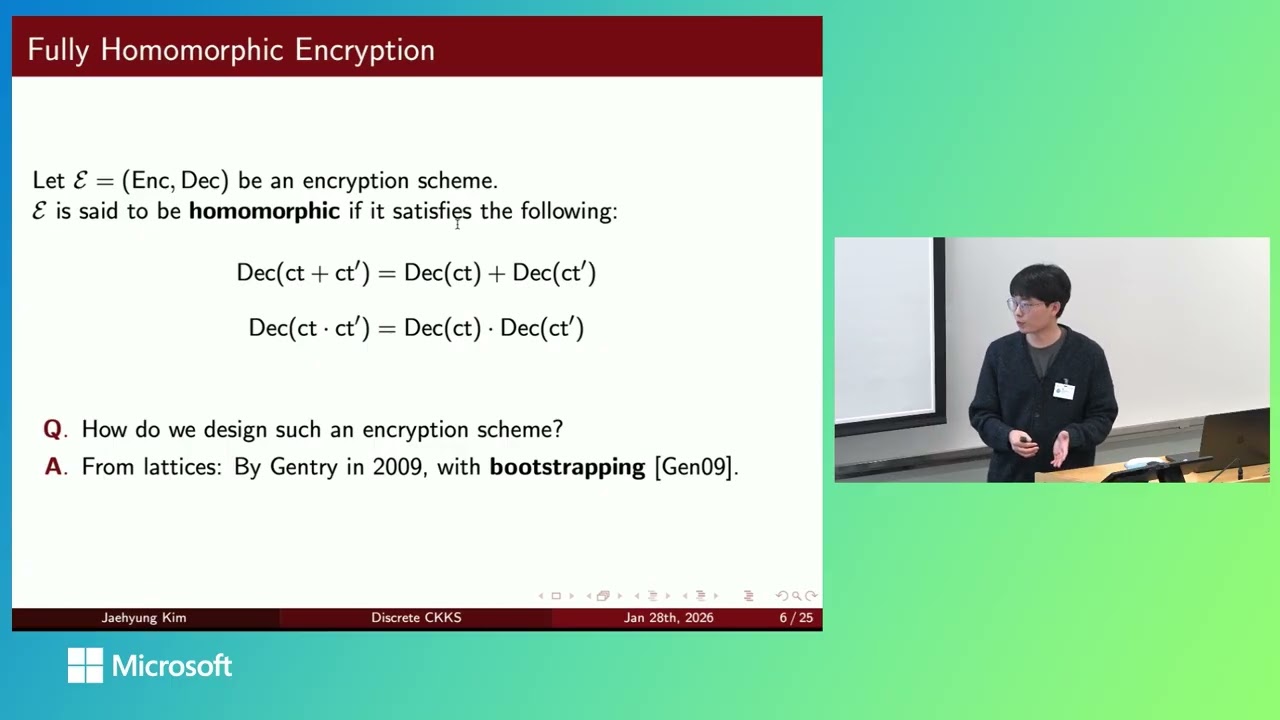
This talk introduces Discrete CKKS, a framework that extends the approximate FHE scheme CKKS to support exact integer arithmetic. It achieves this through a hybrid bootstrapping technique that both cleans noise and raises the modulus, enabling a high-throughput, vectorized engine for general-purpose discrete computations on encrypted data.