The Rush to Adopt AI: How to Get it Right & Business Risks • Nick Selby & Sarah Wells • GOTO 2026
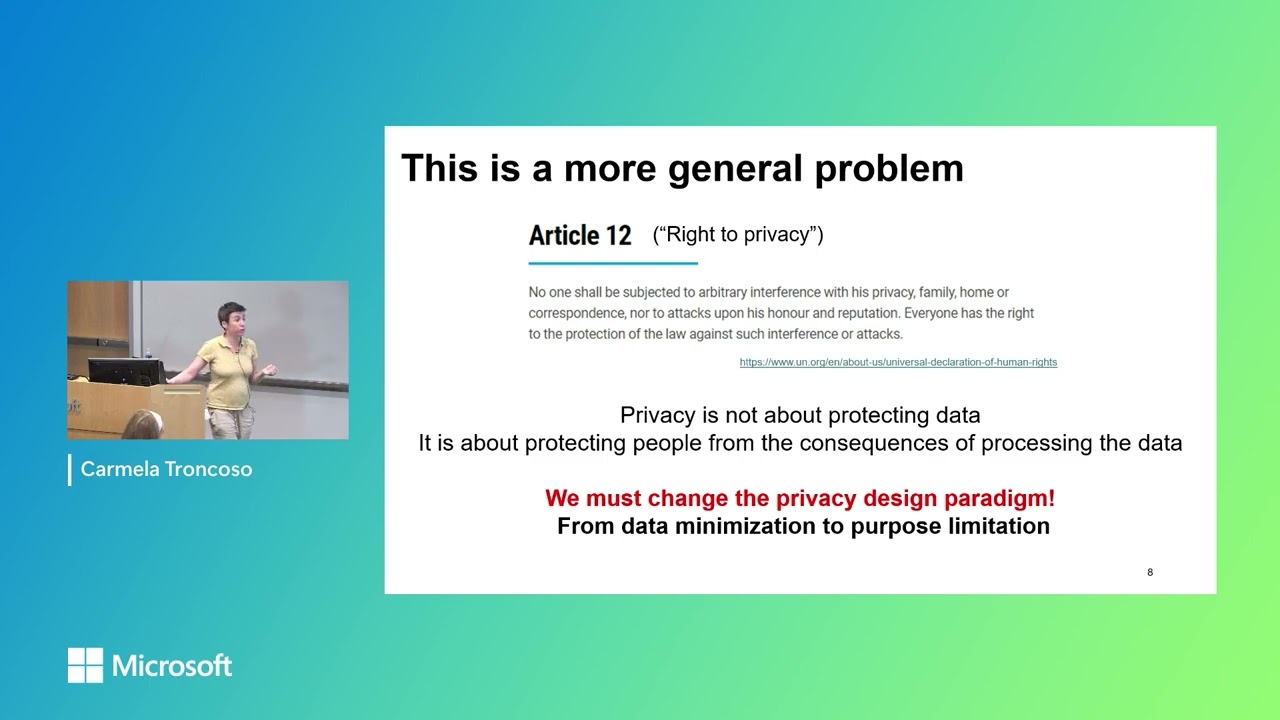
In this interview, Sarah Wells and Nick Selby discuss the significant business risks introduced by the current rush to adopt AI. They cover how AI vendors blur security terminology, how the insatiable need for data creates an enormous blast radius for breaches, and provide a framework for responsible AI adoption through threat modeling, cross-disciplinary governance, and a return to IT fundamentals.