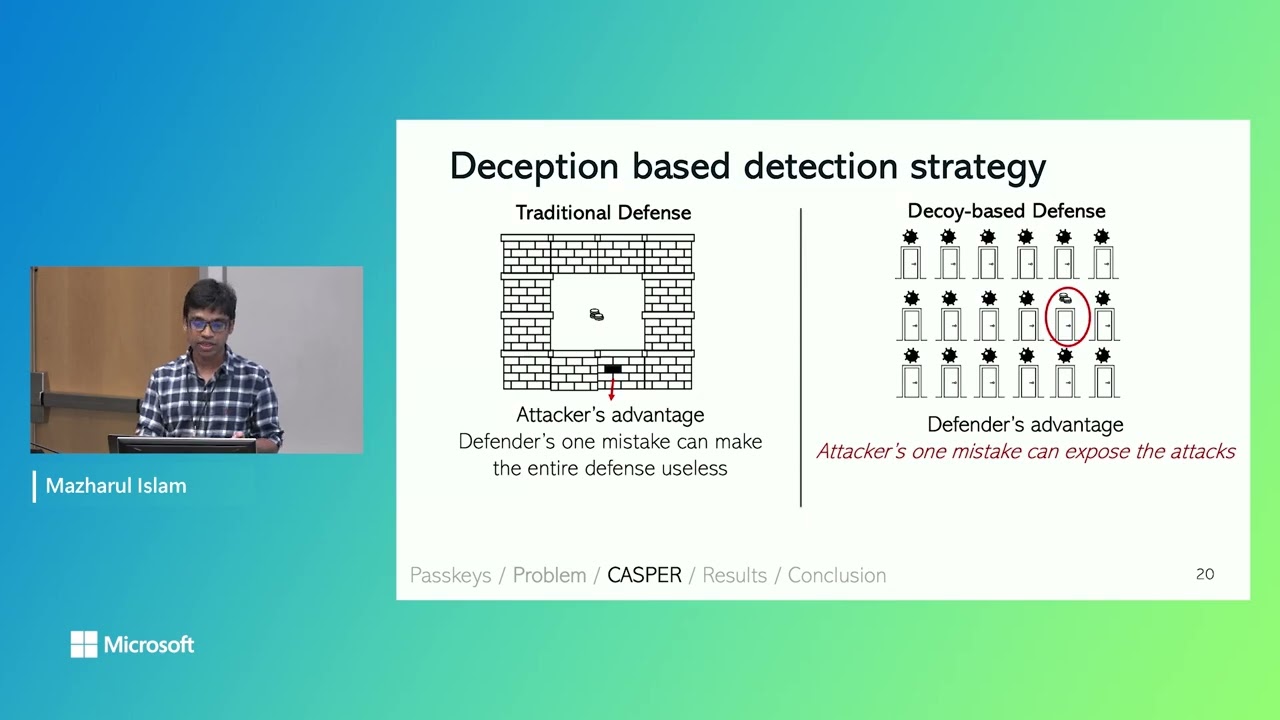
Ransomware whack-a-mole, AI agents as insider threats and how to hack a humanoid robot
A discussion on the evolving cybersecurity landscape, covering the persistent threat of ransomware gangs adapting with AI, the critical failures in identity security highlighted by the Zestix case, the emergence of AI agents as a new class of insider threats, and the physical-world risks demonstrated by hacking humanoid robots.